Palo Alto Networks - Active Directory authentication (via Kerberos) configuration
In order to use your Active Directory accounts to log on to your Palo Alto Networks firewall, you have to configure the firewall to poll your domain controllers via Kerberos. Assuming that you’re running PANOS 5 or higher, the Kerberos agent is built-in and very easy to configure for access.
What you’ll need:
The IP addresses and host names of the domain controllers you want to query (pick at least 2)
The domain name of the domain your accounts are in
A list of the Active Directory accounts you want to grant access to
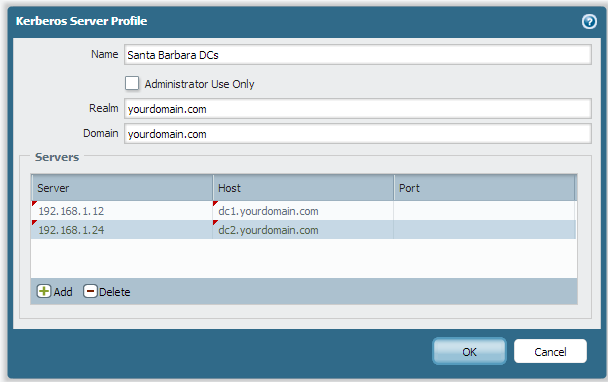
Make a new Kerberos Server Profile
The first step is to visit the Kerberos Server Profiles section under the Device tab. We’ll want to Add a new Kerberos Server Profile.
Make sure that the realm and domain match your Active Directory domain. In most cases, these should match.
When adding servers to the list, the server column is for the IP address, while the host column is for the DNS name. You don’t need to specify a port number if you’re using regular Active Directory domain controllers for authentication.
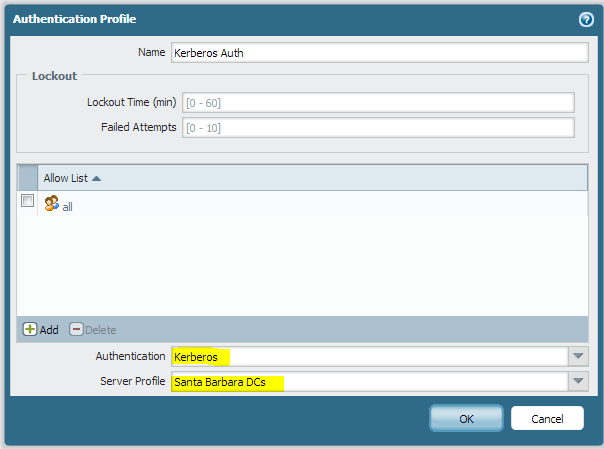
Make a new Authentication Profile
Now we’ll be visiting the Authentication Profile section under the Device tab. We’ll want to Add a new Authentication Profile.
As you can see, I selected the authentication method of Kerberos, and I chose the Server Profile that we made in the last step. I leave the Allow List with the default ‘all’ group active, since we’ll be restricting access later. This doesn’t give everyone access to the firewall, it just gives everyone access to the authentication method.
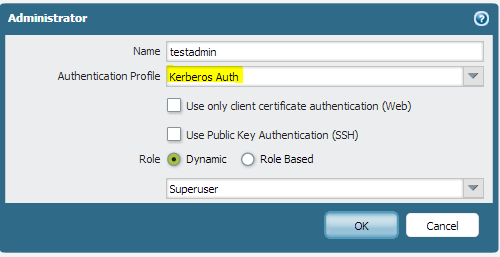
Add your administrators
Finally, we’ll be using the Administrators section under the Device tab to Add a new Administrator.
The name that you use here is the user’s Active Directory account name. For example, my account is often ‘ccadmin’ or something similar. Choose the Authentication Profile that you just created to allow the user to log on via Active Directory. Finally, choose the role/access you want to give this user. The ‘Superuser’ role is the highest level of permissions and has the ability to add and remove other administrators. The ‘Device Admin’ role can do anything on the box EXCEPT manage other administrators. You can also use the Role Based access to define more granular permissions and roles.
Log on with your new account
Now you’ll be able to use your simple username and password to manage your firewall.