Palo Alto Networks - Understanding NAT and Security Policies
When creating your NAT Policies and Security Policies on a Palo Alto Networks firewall, you have understand how the Palo Alto runs the packet through its various filters. I found a great Palo Alto document that goes into the details, and I’ve broken down some of the concepts here.
NAT policies are always applied to the original, unmodified packet
For example, if you have a packet that arrives at the firewall with:
Source IP: 192.168.1.10 (your private)
Destination IP: 8.8.8.8
then your NAT policy must have those IP addresses listed. Similarly, for incoming traffic, say from:
Source IP: 8.8.8.8
Destination IP: 206.125.122.101 (your public)
then you must have those IP addresses in the NAT policy. Notice that for incoming traffic from the internet, you use your public IP address in the Destination field, not the private IP address.
NAT policies always match the original packet’s zone and IP information
For that same incoming packet, the policy will read:
Source Zone: Untrust
Destination Zone: Untrust
While this seems counterintuitive at first, you have to realize that the original packet has a public IP address for both its source and destination IP addresses, and public IP addresses all live in your Untrust zone. The NAT policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather where it came from.
Security policies are similar, as they also reference the original packet’s IP information before any NAT has been applied. So, for an inbound security policy, you would use:
Source IP: 8.8.8.8
Destination IP: 206.125.122.101
just like in the NAT policy. However, in security policies, you have to reference the translated destination zones. Assuming that you’re translating that public IP address to a private IP address, your security policy would use:
Source Zone: Untrust
Destination Zone: Trust
since the translated IP (which you’re NOT referencing in the policy) is in the Trust zone. For some environments, your Destination Zone could be a DMZ instead.
Here’s a cheat sheet:
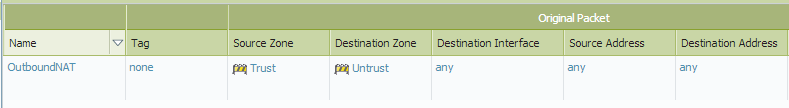
Outgoing Traffic
NAT Policy:
Source Zone: Trust
Destination Zone: Untrust
Source IP: Original Private IP
Destination IP: Original Destination IP
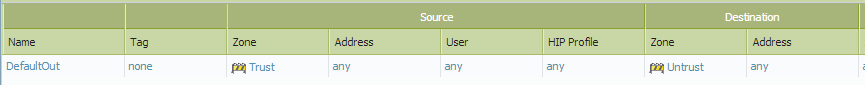
Security Policy
Source Zone: Trust
Destination Zone: Untrust
Source IP: Original Private IP
Destination IP: Original Destination IP
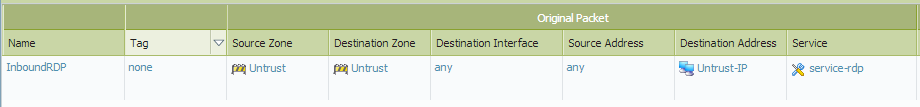
Incoming Traffic
NAT Policy
Source Zone: Untrust
Destination Zone: Untrust
Source IP: Original Public IP
Destination IP: Original Public IP
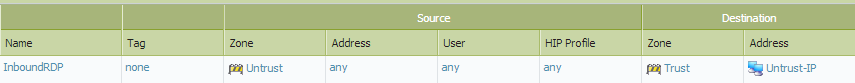
Security Policy
Source Zone: Untrust
Destination Zone: Trust
Source IP: Original Public IP
Destination IP: Original Public IP
Hairpin Traffic
(internal clients accessing internal resources via public IPs)
NAT Policy
Source Zone: Trust
Destination Zone: Untrust
Source IP: Original Private IP
Destination IP: Original Public IP
Translated Source IP: Your Untrust Interface/Public IP
Translated Destination IP: Translated Private IP
Security Policy
Source Zone: Trust
Destination Zone: Trust/DMZ
Source IP: Original Private IP
Destination IP: Original Public IP