Palo Alto Networks – User-ID agent configuration
The Palo Alto Networks firewall can detect the Active Directory names of users on a network and match those names against security policies. A User-ID agent will check the Active Directory domain controllers for Event Log entries that are generated that contain user names and their client IP addresses. Using this information, you can make rules that filter traffic based on particular users (or groups), allowing you to fine-tune your policies.
What you’ll need:
The User-ID agent software from the PAN support site (optional, recommended)
A Windows server to install the User-ID agent on (optional, recommended)
A domain admin account for polling the domain controllers (or a service account)
Install the User-ID agent
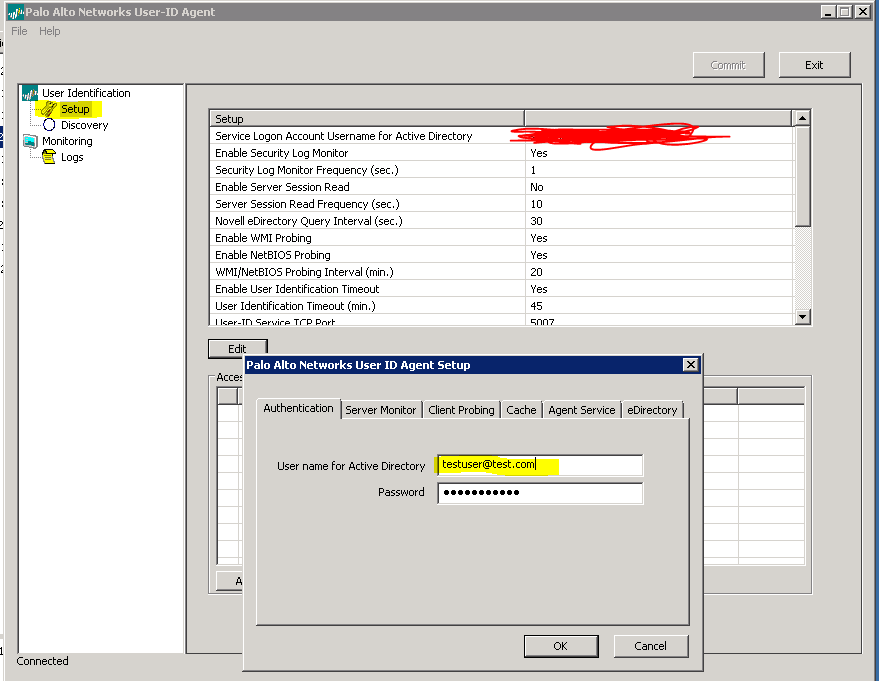
Download and install the User-ID agent on a Windows server. I prefer using an agent on a server rather than using the built-in firewall agent, as it reduces the usage on the firewall and offloads it to the agent.
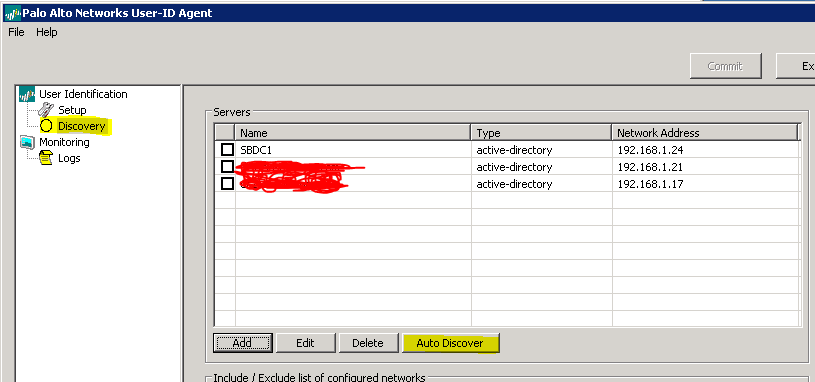
You’ll want to edit the settings to fill in your Active Directory administrator account. You can leave the rest of the settings at their defaults. Next, visit the Discovery tab to select the domain controllers you want to poll.
If you hit the auto discover button, it will find all of your domain controllers. Make sure to add any that it missed, or to delete any that you don’t want to poll. That should be all the config you need on the agent.
Configure the User-ID Agent
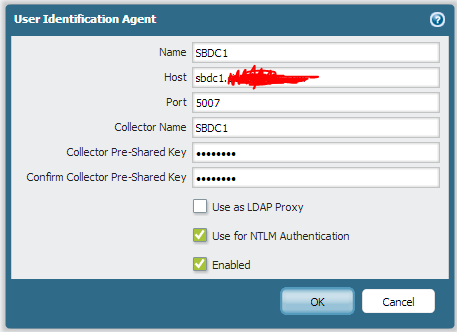
The next step is to add a new User-ID Agent in the User-ID Agents tab in the User Identification section under the Device tab.
Port 5007 is the default User-ID agent port, so make sure to punch that in. You shouldn’t need a pre-shared key, but I filled one in anyway. Now you can use Active Directory user names in your policies, or you can set up an LDAP server profile to do group-based mapping.