Consoles, Enterprise Firewalls, and UPnP
Like many IT professionals, I have a home lab. The ability to test new technologies and ideas in the comfort of your own home without taking down a production environment is great. There’s a ton of enterprise tech that has free or very cheap licensing for home use, like the Juniper Firefly Perimeter (SRX) VM, vSphere Hypervisor (ESXi single-host), and several others. You can also get used servers and networking gear from a variety of sources to let you emulate an enterprise environment.
Unfortunately, gaming consoles don’t work well with enterprise configurations and hardware at home. Consoles like the PS4 or XBONE assume that your network follows an ubiquitous setup: a single modem/router/WAP provided by your ISP. UPnP is considered table stakes for routers in the home consumer market. Without UPnP, many games and applications don’t work without a lot of troubleshooting and tedious port forwarding. Peer-to-peer multiplayer (P2P) and voice chat are the two most common offenders.
However, there’s a way to get the best of both worlds: an enterprise firewall at the edge with cool features like logging, user-based policies, layer-7 inspection, and the rest, while still being able to play multiple consoles and games without any issues.
It’s called Double NAT.
Double NAT
First, credit for this design goes to my friend Jeff Ford, who introduced it to me as “the dirtiest thing [he’d] ever done”. I use it at home and it works.
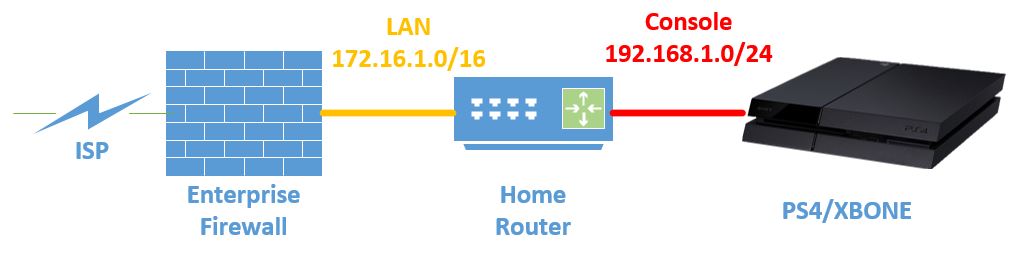
Double NAT is usually a bad word for network engineers. However, I am a believer that you should use the best tool for the job, even if it’s an awful tool . The key to the double NAT solution is to leverage the UPnP capabilities of your typical home router to automatically create port forwarding rules. Essentially, you put a home router (like my favorite, the Asus RT-AC66U) behind your enterprise firewall (like my Palo Alto VM100).
The home router’s Internet port sits on your LAN, with the enterprise firewall as its default gateway, as if you were an ISP. The router’s LAN ports are your custom console network, which should be a different RFC 1918 subnet from your actual LAN. The firewall feature on the router should be disabled, as well as web or admin access on the Internet port. It should be configured in “router” mode as opposed to a bridge or AP mode. I also turn off wifi, as my consoles are wired directly.
On the enterprise firewall, you be creating a NAT rule that sends all possible ports to the home router. Put it at the bottom of your NAT/PAT list so that your actual port forwarding takes precedence. Anything that you’re not manually creating a PAT entry for will be translated and sent to the home router.
The home router receives port forwarding requests from your consoles, and then configures its own PAT table for those ports. The home router thinks it is directly connected to the internet even though you’re using RFC 1918 space for its Internet interface. The router has no idea that you’re doing the translation in front of it with the enterprise firewall. When traffic comes in to the home router, it will use its port forwarding table to send traffic to the proper console.
Example
- Enterprise Firewall untrust interface set to your public IP from your ISP
- Enterprise Firewall trust interface is
172.16.1.1/16 - Home Router internet interface is
172.16.1.100/16 - Home Router internet default gateway is
172.16.1.1/16(the firewall) - Home Router LAN interface is
192.168.1.1/24 - Home Router is in
routermode with firewalling turned off - Consoles are plugged into Home Router LAN ports
- Console IPs are provided via DHCP by the Home Router
- Enterprise Firewall has a 1:1 NAT rule at the bottom, mapping all incoming traffic to
172.16.1.100
Example code from Junos:
set security nat static rule-set console-nat from zone untrust
set security nat static rule-set console-nat rule rule1 match destination-address PUBLIC_IP/32
set security nat static rule-set console-nat rule rule1 then static-nat prefix 172.16.1.100/32
Example from Palo Alto Networks:
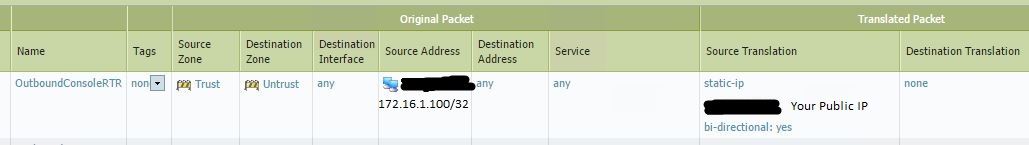
set rulebase nat rules OutboundConsoleRTR to Untrust
set rulebase nat rules OutboundConsoleRTR from Trust
set rulebase nat rules OutboundConsoleRTR source ConsoleRouterIP (172.16.1.100)
set rulebase nat rules OutboundConsoleRTR destination any
set rulebase nat rules OutboundConsoleRTR service any
set rulebase nat rules OutboundConsoleRTR nat-type ipv4
set rulebase nat rules OutboundConsoleRTR source-translation static-ip bi-directional yes
set rulebase nat rules OutboundConsoleRTR source-translation static-ip translated-address YOUR_PUBLIC_IP